
Available at
Untrusted: Hackers at Large - Review
Table of Contents
- Introduction
- Gameplay and Mechanics
- Crew Management and Character Development
- Hacking System and Realism
- Narrative Structure and Choices
- Graphics and Atmosphere
- Replay Value and Long-term Motivation
- Conclusion
Introduction
The cyberpunk gaming landscape has gained a remarkable addition with "Untrusted: Hackers at Large." Following the success of the original Untrusted universe, this single-player adventure pushes the boundaries of what a hacking game can be. Developed as a strategic RPG with strong focus on authentic cybersecurity elements, the game promises an experience that should appeal to both tech enthusiasts and strategy fans alike.
Gameplay and Mechanics
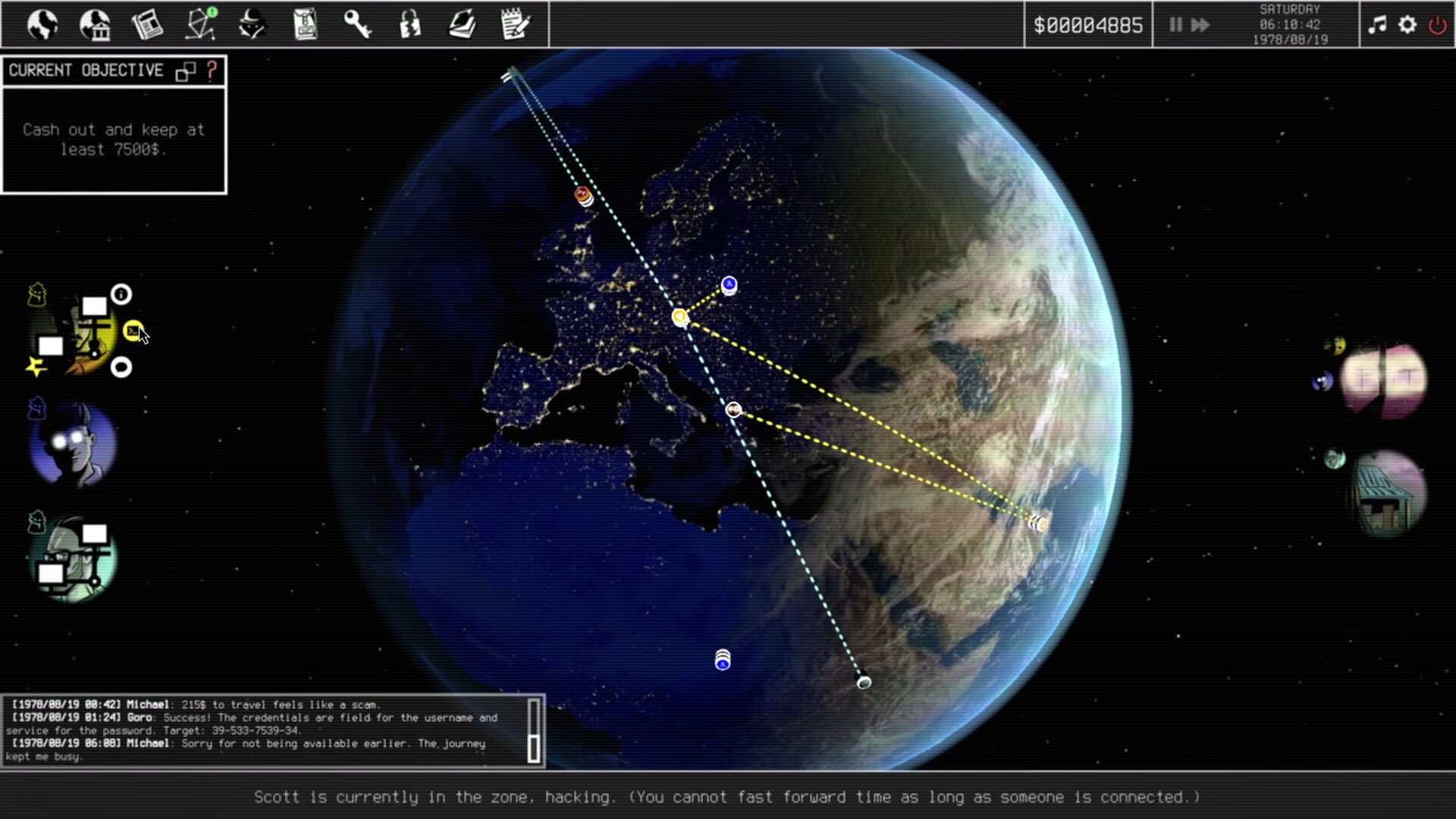
The heart of "Untrusted: Hackers at Large" lies in its multi-layered approach to the hacking genre. Unlike superficial "puzzle solvers," the game demands genuine strategic thinking. Every system infiltration requires careful planning: What tools do I need? How high is the detection risk? What's my exit strategy?
The mission structure follows a non-linear approach that offers different solution paths for each objective. You can opt for the direct but risky route or choose subtle, time-consuming methods. This flexibility makes each mission a unique puzzle.
Crew Management and Character Development
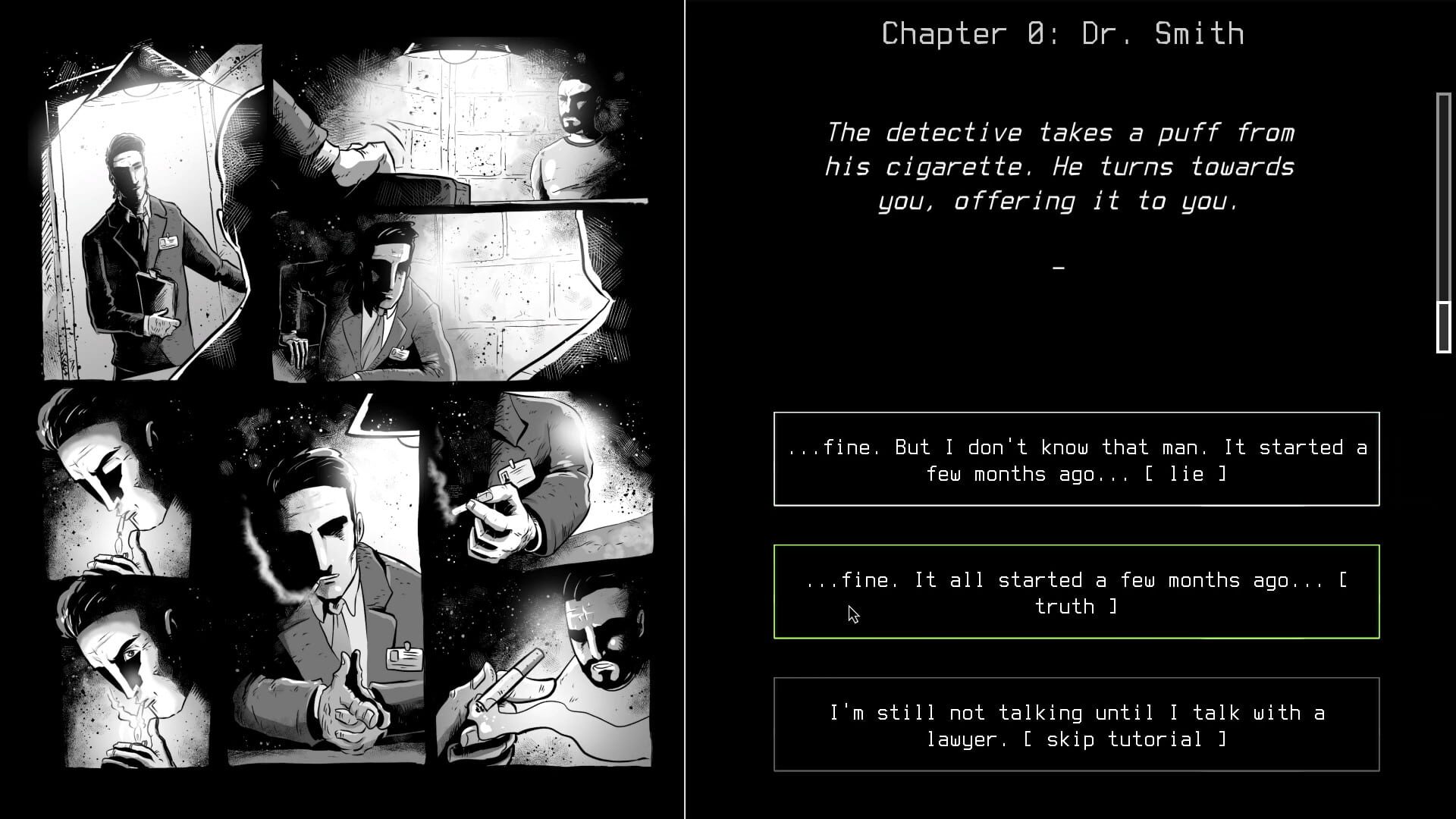
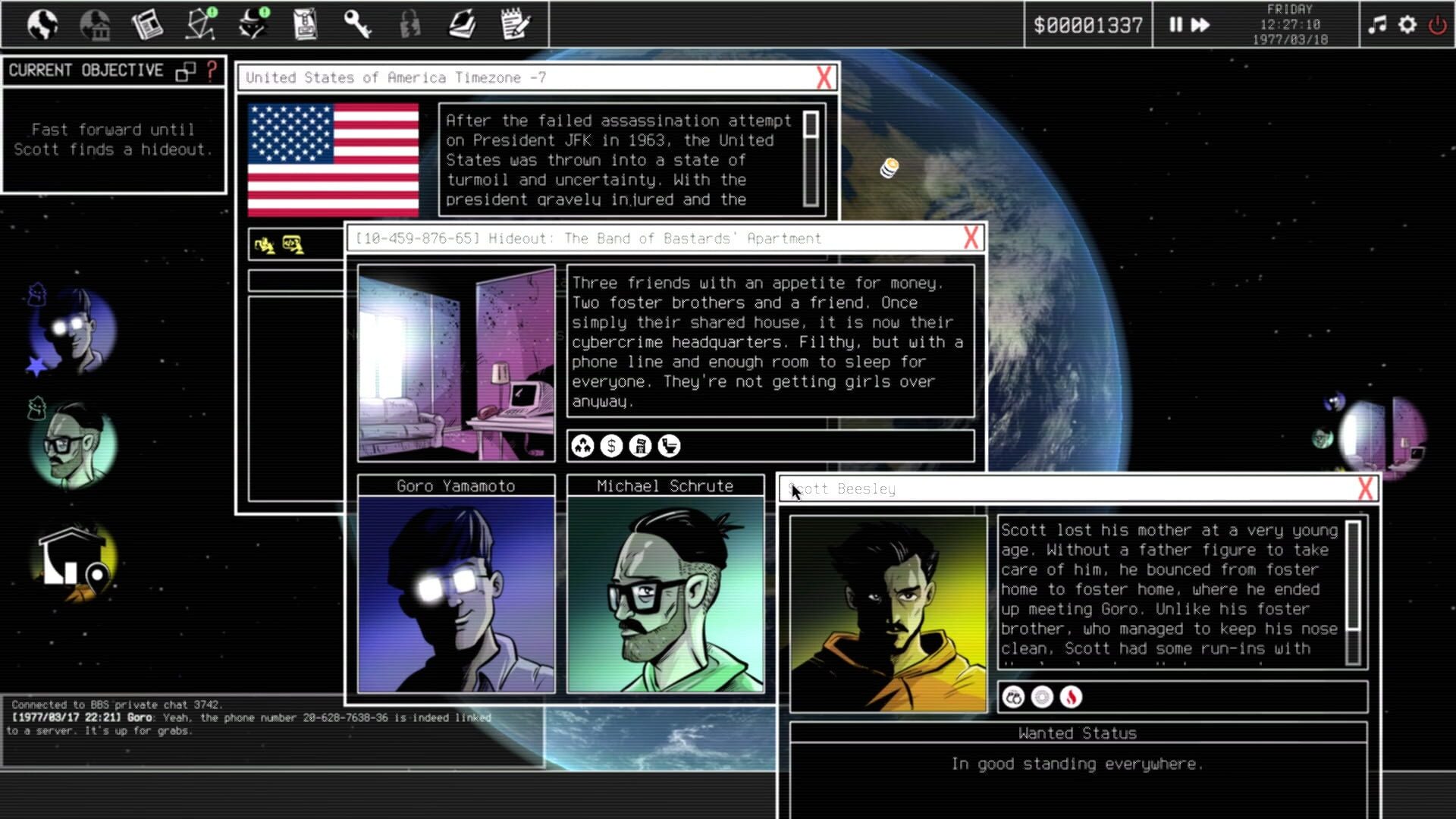
A particular highlight of the game is the crew management system. Each hacker in your team brings special abilities: The social engineer can gather information through human contacts, while the code specialist cracks complex encryptions. Character development goes beyond simple skill points - every decision shapes the personality and loyalty of your team members.
Particularly fascinating is the risk-reward system in personnel management. Aggressive tactics may be successful short-term but can undermine team trust in the long run. This psychological component gives the game unexpected emotional depth.
Hacking System and Realism
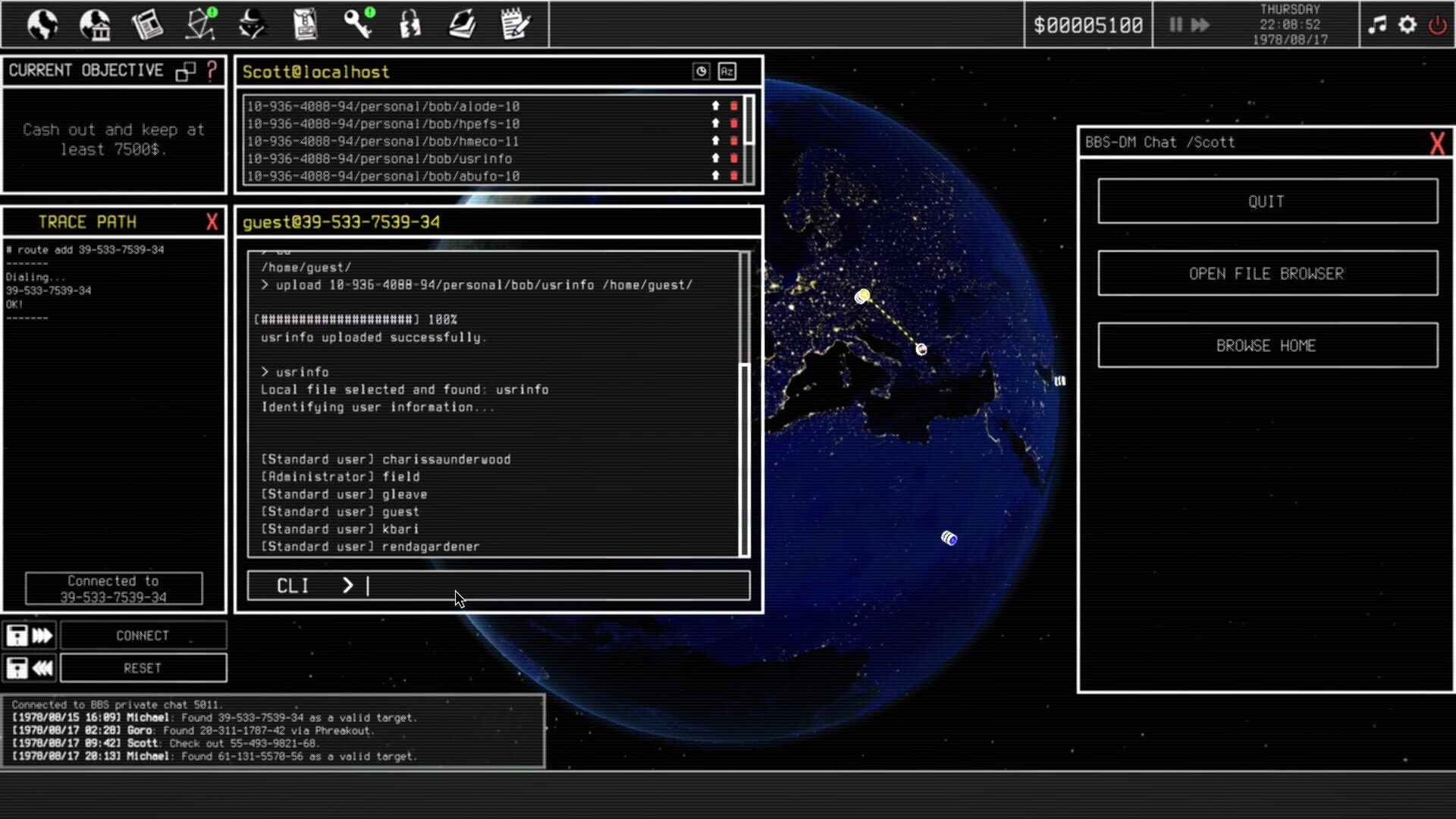
The technical aspect of the game deserves special recognition. The developers have obviously conducted extensive research to portray authentic hacking methods. From SQL injection to social engineering - the techniques used in the game are based on real cybersecurity concepts.
The game remains accessible to non-technical players without diluting complexity. An intelligent tutorial system gradually introduces various hacking methods, while experienced players can dive directly into deeper mechanics.
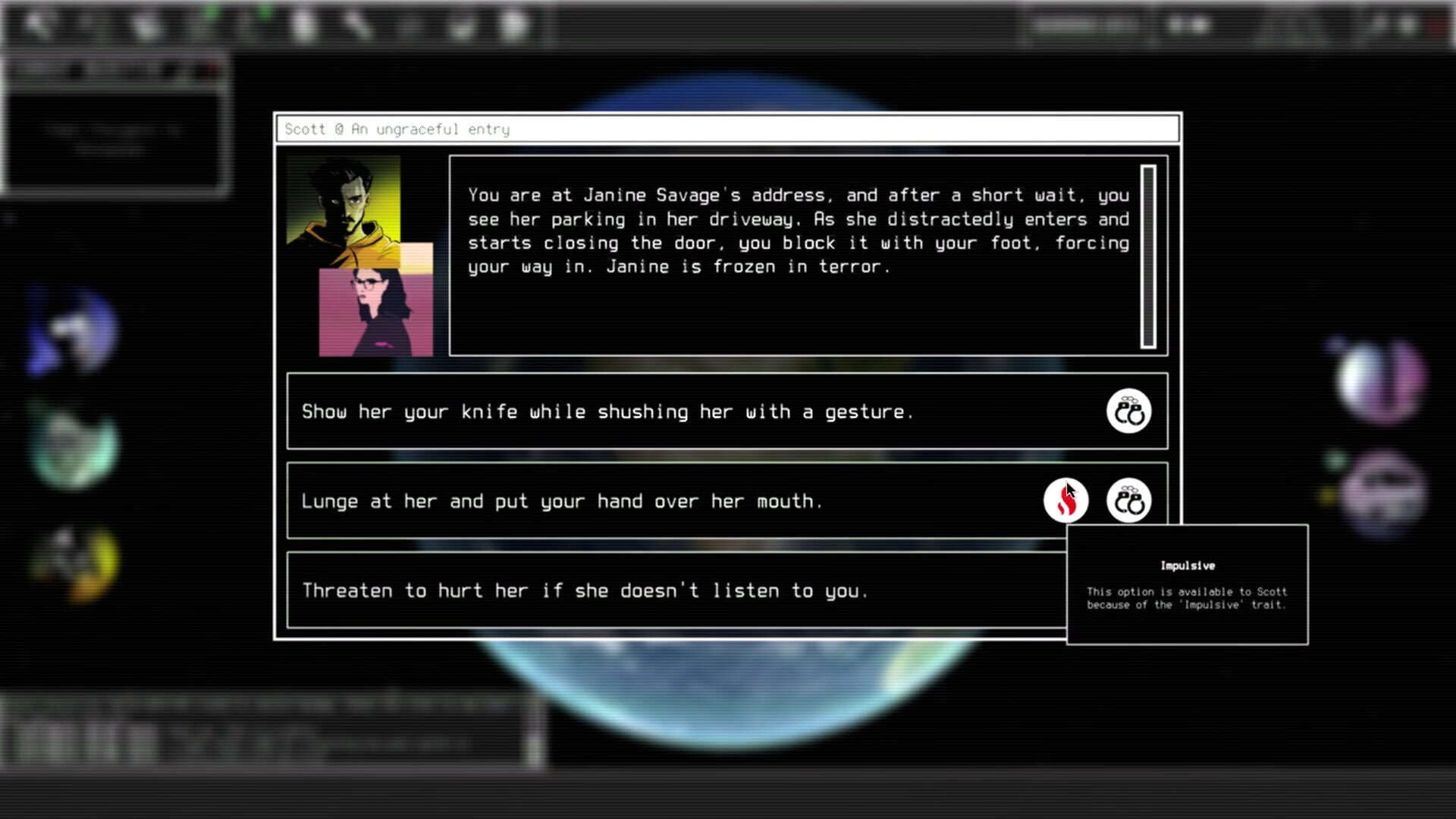
Narrative Structure and Choices
The story of "Untrusted: Hackers at Large" unfolds through player actions. Each mission influences not only the immediate plot but also the larger narrative. The moral gray areas are particularly well-crafted: Is it justified to blackmail a corrupt politician if innocent people might suffer?
The choice systems avoid simple good-evil dichotomies in favor of nuanced consequences. Decisions often don't manifest until many hours later, leading to surprising plot twists.
Graphics and Atmosphere
Visually, the game employs a stylized neo-noir look that perfectly matches the dark cyberpunk atmosphere. The user interfaces are functionally and aesthetically pleasing without being overwhelming. Particularly successful are the hacking sequences, which visually remind of real terminal environments.
The sound design effectively supports the tension. Subtle electronic sounds amplify stress during critical hacking moments without being intrusive.
Replay Value and Long-term Motivation
Thanks to multiple solution paths and decision possibilities, "Untrusted: Hackers at Large" offers considerable replay value. Different crew compositions lead to varying gameplay experiences. Procedurally generated side missions additionally provide variety.
The difficulty curve is well-balanced, with advanced players able to pursue more complex targets with higher rewards.
Conclusion
"Untrusted: Hackers at Large" sets new standards for hacking games. It combines authentic technical elements with strategic depth and narrative complexity. While minor balance issues and occasional repetitions slightly mar the overall impression, the strengths clearly outweigh the weaknesses. This is a game for thinkers, strategists, and anyone who has ever wanted to know what it feels like to be a digital phantom.
System Requirements
Minimum
Recommended
Das könnte dich auch interessieren
Weitere Reviews aus der Kategorie game.

Inhaltsverzeichnis 1. [Einleitung](einleitung) 2. [Gameplay und Mechaniken](gameplay-und-mechaniken) 3. [Storytelling und Charakterentwicklung](story...

Solargene Review Inhaltsverzeichnis - [Einleitung](einleitung) - [Gameplay und Mechaniken](gameplay-und-mechaniken) - [Technologie und Forschung](t...

Bound City Review Inhaltsverzeichnis 1. [Einleitung](einleitung) 2. [Atmosphäre und Weltdesign](atmosphäre-und-weltdesign) 3. [Gameplay und Mechani...